Fraud costs don’t start in your finance department. They start in your IVR, online, and occur inside and outside of your contact center. While you are aware of the media reported mega-breaches that plague companies and consumers both, have you considered your contact center’s place in the journey from data capture to fraudulent transaction and account takeover? Fraudsters stalk contact center IVRs using them as search engines for your CRM to validate customer data. They then use that validated customer data to social engineer your agents or commit fraud across other channels.
If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle.
― Sun Tzu, The Art of War
To help support contact center leaders in the arms race for customer data, Pindrop has assembled a curated collection of assets, research, and tools to help you bolster your defenses.
The Journey of a Fraudster
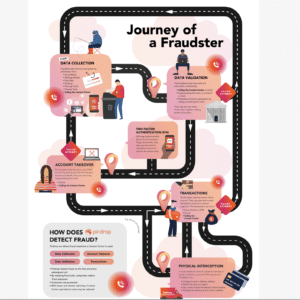
You can detect, predict, and mitigate fraud inside and outside the contact center. Get exclusive tools, actionable insights, and trend analysis to keep you prepared and protected against Contact Center Fraud.
Fraud In The IVR

You can harness the power of your IVR in the form of predictive analytics. Learn more about preventing fraud in the IVR and learn how you can harness data from your phone channel to harden your entire contact center to attack.
Fraudster Profiles

Fraudsters don’t rely on luck; they do their homework. They use multiple sources like purchased data, harvested from corporate breaches, and sold on the dark web and leaked data scraped from servers and unsecured pages to develop profiles on the organizations they target. They study how contact centers operate, the relevant policies for their endeavors, and have access to petabytes of personal data on their customers like name, DOBs, SSN, drivers license numbers, and more. They come prepared to answer security questions and have practiced strategies to bypass your security, authenticate into account, and get out before anyone notices. Pindrop is turning the tables on fraudsters by creating a playbook to stop them.
See more Fraudster profiles here.
Fraudster Toolkit
Fraudsters use tools just like you do to help them optimize their performance. So we developed resources to help you build solid defenses. Below are the most popular tools fraudsters are using to cost you money, time, and customers – with links to show you how to stop it.
The Wire Cutters: Social Engineering
One of the core components of contact center fraud, but almost impossible to detect consistently without technology. Learn More – Webinar on demand
The Circular Saw: Voice Distortion
Many fraudsters alter their voice to bypass any voice biometric technology trying to create noise, or even as simple as using a higher or lower pitched voice to more closely imitate their victim when talking to a contact center.
The Framing Hammer: Fraud Bible
As a possible legend or myth the fraudster playbook known as the fraud bible, read Pindrop’s position on the darkweb trophy.
The Tape Measure: Data on Target Victim
Data reconnaissance and data dealing can mean big business for fraudsters, learn more about their techniques here and how they supplement their own data with your IVR.
The Shovel: Account Mining
Fraudster can even use a company’s own tools against them. Watch how fraudsters use the IVR to verify stolen data, and use automated dialers to dial account numbers and PINs.
The Handyman: Artificial Intelligence
AI is changing the world rapidly, including fraud. AI now has provided the ability to look and sounds like anyone else. If someone has a long youtube video of themself, that would be enough to replicate their voice and allow the fraudster to communicate as the victim to employees and contact center.



