With each new generation of smartphone, manufacturers are adding more and more sensors to enhance the user’s experience, but this also means that more and more apps are asking for blanket permission to use those sensors. This proliferation of sensors and permissions is creating serious privacy and security issues, as researchers at Newcastle University established with a new attack the can recover a user’s four-digit phone PIN 94 percent of the time by measuring the output from an Android device’s motion and orientation sensors.
The technique, outlined in a paper published earlier this month, uses a Javascript-based side channel attack called PINlogger, that reveals users’ PINs with 94 percent accuracy within three tries. PINlogger can access data through a number of ways, including iframes in mobile browsers such as Chrome, Firefox and Safari. This can even occur in the background, as the script can gain access to the sensors even through inactive browser tabs. The paper finds that many times browsers do not implement policies with regards to access to mobile sensor data, primarily because W3C specifications mention nothing about it.
“In this attack, once the user visits a website controlled by an attacker, the JavaScript code embedded in the web page starts listening to the motion and orientation sensor streams without needing any permission from the user. By analysing these streams, it infers the user’s PIN using an artificial neural network,” the researchers said in the paper, entitled “Stealing PINs Via Mobile Sensors: Actual Risk Versus User Perception”.
“Based on a test set of fifty 4-digit PINs, PINlogger.js is able to correctly identify PINs in the first attempt with a success rate of 74% which increases to 86 and 94% in the second and third attempts, respectively. The high success rates of stealing user PINs on mobile devices via JavaScript indicate a serious threat to user security.”
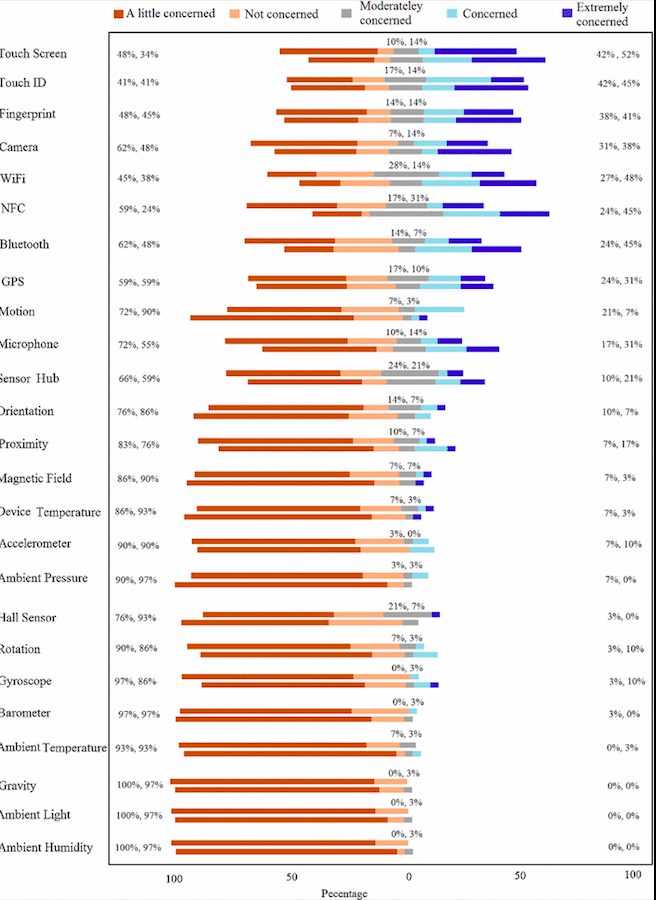
Modern mobile devices include a number of different sensors, such as accelerometers, GPS sensors, and many others. Lots of apps use these for legitimate purposes, including geolocation, measuring speed and direction, and sensing ambient light. But some apps and websites abuse these sensors to gather information about a user’s location activities. In their paper, the Newcastle University researchers also report the results of a study that measured the public’s perceptions of mobile sensor stacks and came back with a universal result that people were not away of the sensors on their mobile phones and other devices. And more importantly, they found that users are not concerned about these sensors.
The study surveyed more than 100 people and found that many of the sensors didn’t cause any concern for most users, with the exception of fingerprint sensors. The results (seen below) show that most users aren’t much concerned with the risk of most of the sensors in their mobile devices.
The attack that the researchers developed using PINlogger.js relies on output from a number of different sensors in a target Android device. It assumes that the victim is using a digit-only PIN typed on a soft keyboard on a screen.
“Unlike similar works which have to gain the access through an installed app, our attack does not require any user permission. Instead, we assume that the user has loaded the malicious web content in the form of an iframe, or another tab while working with the mobile browser. At this point, the attack code has already started listening to the sensor sequences from the user’s interaction with the phone,” the paper says.
At the present time, there does not seem to be a solution for the problem. The paper does come forward with a suggestion: “Having control on granting access before opening a website and during working with it, in combination with a smart notification feature in the browser would probably achieve a balance between security and usability.” This is similar to many other mobile applications where a user must grant an application access to give the user notifications or use his location.
Maryam Mehrnezhad, one of the paper’s authors, said via email that the problem will get more serious over time.
“When smart kitchens, smart homes, smart buildings, and smart cities are equipped with multiple sensor-enabled devices connected via IoT,” Mehrnezhad said, “these devices will be constantly sensing people and their surroundings and broadcasting this information. If sensors are not securely managed, the threat is going to be much bigger.”