Article
Largest IRS Phone Scam Exceeded 450,000 Victims
Vijay Balasubramaniyan
April 15, 2014 (UPDATED ON October 31, 2025)
Peter Casanova, Raj Bandyopadhyay
7 minutes read time
The IRS is warning people about the “largest ever” phone fraud scam targeting taxpayers. In the interest of learning more about this phone-based threat, Pindrop has investigated the attacks and, among other things, we have successfully posed as a victim and recorded the call. What follows is the complete audio and transcript of the interaction, and our analysis of some of the tactics that these fraudsters are employing. Note that in the audio files, we have distorted the voice of the victim (a Pindrop employee) to protect their identity.
Findings
Attackers are using magicJack VoIP phone numbers for consumers to “call back” as part of this attack. There is no reason to believe magicJack is in any way complicit with these attacks.
The attackers appear to be operating out of India and are seeking approximately $5,000 per successful attack.
The attackers are asking consumers to use GreenDot MoneyPak service to wire money to a Paypal account.
As compared to previous attacks involving impersonation of the IRS, this attack involves much higher volumes, with complaints in excess of 10 times higher than previously seen. We estimate the number of attack calls has already likely exceeded 450,000 in March.
Setup
The fraudsters use classic call scam techniques: they use a spoofed Caller ID that looks legitimate; they use urgency and threats to keep the caller on the line and force them to act quickly; they leave behind different numbers for “call backs” and they only use these numbers for a limited time.
True to form, the IRS fraudsters made the incoming number appear to be legitimate. Occasionally, they spoof the telephone assistance service number of the IRS, 1-800-829-1040. More frequently, they call from numbers from the same area as the victim, in order to entice the victim to pick up the phone thinking that the call is from someone they know.
As heard in the audio, they try hard to keep the victim on the call. And they leave behind a phone number where they can be reached, known as a “call back” number. Typically, a fraudster buys a large block of numbers from a VoIP provider to serve as these “call back” numbers.
The fraudsters are constantly decommissioning these “call back” numbers. From time to time we also see them call from these numbers directly. In order to engage with them we first needed to identify what set of numbers are being used for this purpose and find one that was not yet decommissioned.
Tracking the attackers
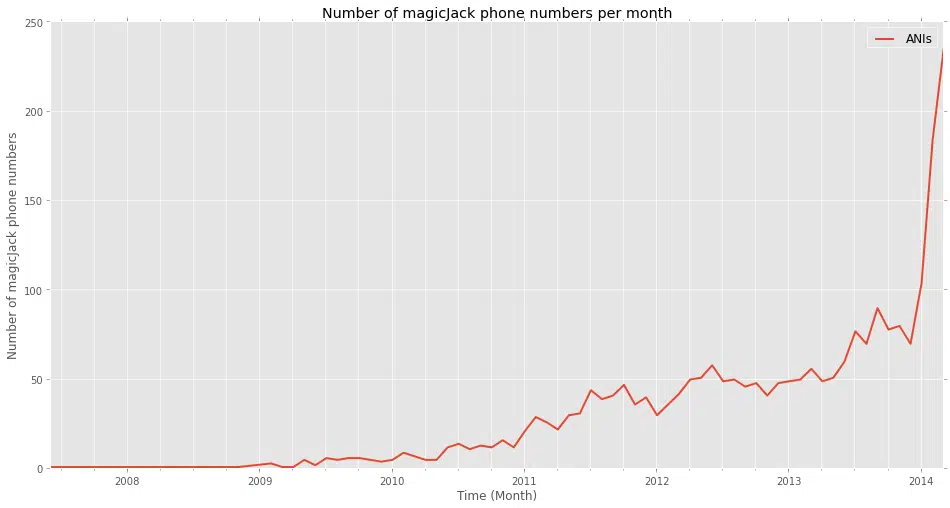
Pindrop maintains the Pindrop Reputation database, the world’s largest collection of phone number data and activity. To identify the phone numbers being used we mined our phone reputation service for IRS related activity. Among the numbers used, the majority was from the magicJack service, an inexpensive, online VoIP service.
The most complained about magicJack numbers were non-toll-free numbers, for example: 202-506-9XXX. The line graph shows the number of magicJack numbers associated with IRS scams over time (the IRS is a consistent target of scams). The data clearly shows that the number of phone numbers has gone up significantly this year. Through March, we have observed 523 numbers perpetrating this scam. The total number for all of 2012 was 780. This supports the IRS’ claim that this is the “largest ever” phone fraud scam.
The number of complaints associated with these numbers has gone up even more drastically this year. Complaints are in excess of 2400 calls this year to date – all of last year the number of complaints we observed was 1047.
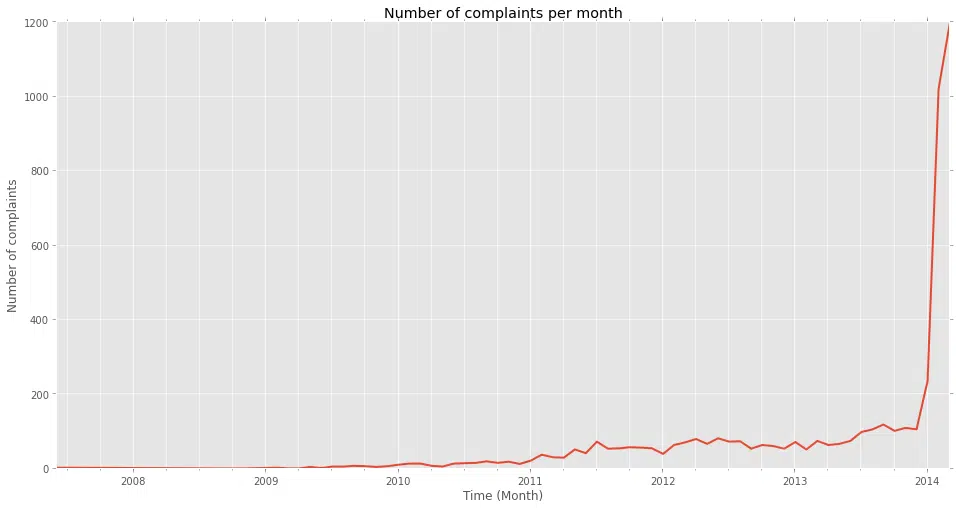
The number of phone numbers and complaints are good indicators that the number of victims being targeted has dramatically increased. In order to roughly estimate how many calls are being made, we can make the assumption that a call takes 5 minutes, which includes leaving voice mails and live conversations. That adds up to 12 calls an hour. We assume an 8 hour work day for each caller and that each caller is using one of the numbers. Therefore, each number could be making 96 calls a day. At 235 total numbers observed in March, the number of calls made could potentially be in excess of 450,000 in March.
Where are the attacks coming from?
We identified a smaller set of phone numbers that our systems had indicated were still active in this scam. We then looked at what time of day these numbers are most active. We used that to maximize our chances of interacting with these fraudsters. As seen in the temporal activity graph below these fraudsters work east coast hours.
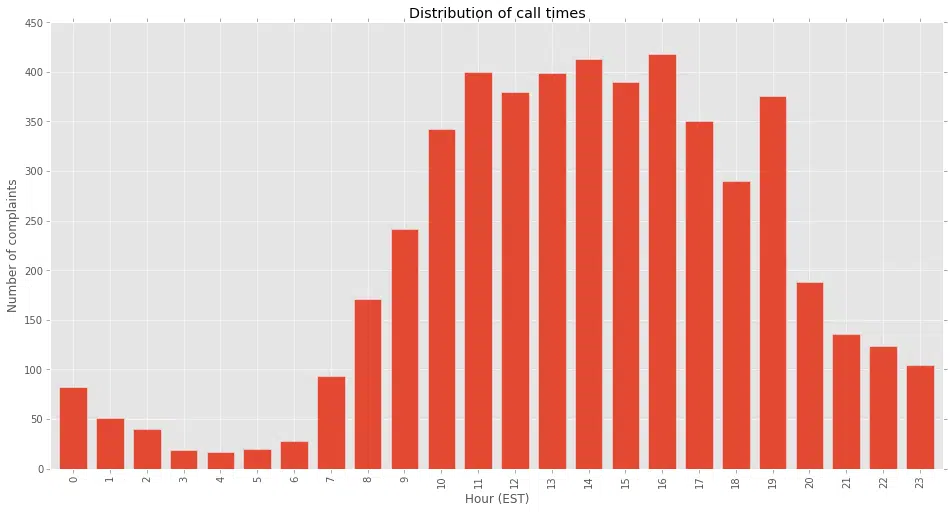
To determine if the attackers are actually operating in the Eastern US, we analyzed the call audio with Pindrop’s phoneprinting technology, which, among other things, can determine the origin of a call based on audio artifacts. In this case, the audio analysis showed clearly and consistently that the calls are originating from outside the US and are most likely calling from India.
Using a brand-new phone, which had not been used for any other purpose, we finally called (202) 239-7034 and after a couple of attempts we were talking with the fraudsters.
Interaction
For a rare and engaging window into how phone scams work, we highly recommend listening to the audio. If you’re short on time, read the transcript. We would like to highlight a few moments that we found the most revealing about their modus operandi.
Click on the player for the audio excerpt:
(0:25) – They make some basic checks to determine if the victim is someone they have interacted with previously. We suspect this is to provide the fraudster context to make the conversation real for the victim.
(1:20) – They claim to be the Federal Investigation Department, a legal department working for the IRS
(2:05) – They do NOT target Americans. They are primarily targeting immigrants.
(3:45) – Tries to see if a third party (accountant) files taxes. Claims mistakes in taxes.
(4:01) – Scam starts. Sees if there are any overseas transactions.
(5:32) – Claims $5,868 pending taxes. We created a fake victim and he already owes taxes.
(6:10) – Threat of Arrest Warrant issued.
(7:30) – Get supposed name from scammer “Steve Parker”.
(9:35) – They claim to not accept standard payment types (debit/credit cards), only Tax Pay Voucher from a Government Store such as Home Depot and Food Lion.
(11:50) – Ask for zip code and then get a store close to that zip code.
(13:30) – They settle for $2,400 for warrant cancellation fees when we say we only have $2,600.
(14:20) – They are trying to make the victim stay on the phone while they get the money together.
(17:20) – Transferred to the accounting department “Brian”.
(18:15) – They try to justify why money has to be wired to the restitutions Paypal account via prepaid card.
(20:12) – Their card of choice is GreenDot MoneyPak.
Post-call
After this call, the scammers tried several attempts to call back throughout the night and morning. This was not surprising to us; the scammers probably assumed that they had almost “closed the deal” on this particular victim. However, the next afternoon, our employee received a call alleging to be from GreenDot asking if he had purchased a MoneyPak card recently. The caller stated that to use the card, activation was required and asked our employee to provide him with the number on the back to gain access to the money on the card.
This leads to some really interesting questions: Was this caller really from GreenDot? If so, how did they obtain the phone number that our employee had used, given that we had just acquired this phone and not disclosed its number anywhere? If the caller was not from GreenDot, is this just another play on part of the scammers to obtain the money on the card?
We continue to investigate this attack and monitor these attackers.




