Are you giving
fraudsters your clients’
banking details?
System (IVR), you probably are.

The Fraudster’s Journey
In more than 60% of fraud cases, bad actors used a contact
center -- frequently an IVR -- for pre-crime research. It’s like
casing a bank before a robbery -- only much easier.
Please enter your 16-digit card number.


Research
After purchasing a list of compromised accounts on the dark web, a fraudster calls your customer center to verify which accounts are still active.
Sometimes, they use a bot to auto- matically dial numbers and try to guess the accounts that are active.

Now enter the last four digits of your social security card number.

Verification
A fraudster uses the IVR to test out different combinations of sensitive financial data. There’s no limit to how many combinations he can type into the keypad.
In 3 days, he successfully cracks a customer’s 3-digit CV2 number. In 4 days, he successfully cracks a customer’s 4-digit pin.


Cross channel fraud
Fraudsters take the information leaked in the IVR and apply them to pass authentication in other channels, be that online, in the call center or in person. Suddenly, none of your customer’s finances are safe.
Are you seeing the whole picture?
Only monitoring agent calls could leave you blindsided. Opening monitoring
into IVR helps you see a more complete picture, and protect your
customers accordingly.
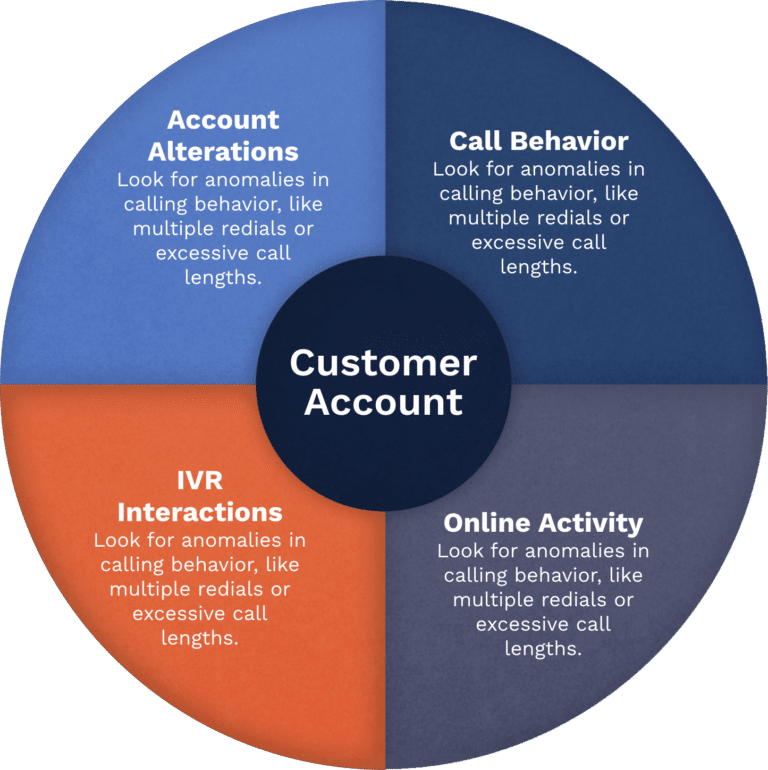
Customer
Account
Account Alterations
Look for anomalies in calling behavior, like multiple redials or excessive call lengths.
Call Behavior
Look for anomalies in calling behavior, like multiple redials or excessive call lengths.
IVR Interactions
Look for anomalies in calling behavior, like multiple redials or excessive call lengths.
Online Activity
Look for anomalies in calling behavior, like multiple redials or excessive call lengths.
To Catch a Fraudster
Pindrop is a leader in IVR fraud protection. To catch fraudsters
in their tracks, we apply machine-learning models from:

50+

8
out
of
10

2 years

1.2B
Pindrop Protect safeguards your IVR

Incoming Calls Scored
Cross-Channel Correlation
High Risk Activity Flagged
Risk-Based Routing
Marked and Monitored
Time is Money
The vast majority of IVR fraud isn’t detected until after a fraudulent
transaction has been made. Pindrop Protect detects suspicious
activity 18 days earlier than agent monitoring alone.
Day 0
Fraudsters call IVR to research (no transaction made yet)
Day 4
Day 10
Day 28
Day 30