The wealth of information housed by contact centers can be leveraged by fraudsters for data mining and cross-channel attacks. In an effort to prevent phone fraud, many businesses implement authentication methods; however, most fail to administer the authentication required to provide a layered defense system. As social engineering and fraud technologies have become more advanced, standard authentication methods have proven to become less sufficient. “You have to assume the criminals can get through one layer [of authentication]; they can get through two, they can even get through three,” says Avivah Litan, Vice President with the consultancy Gartner. “But if you have multiple layers, up to five, and you’re continuously authenticating that user and continuously looking at their activities against their profile, you should be in pretty good shape.”
Multiple layers of security allow organizations to meet regulatory requirements and effectively safeguard customer data. Knowledge-based authentication (KBA), has served as a standard authentication method for years; however, 10-15% of KBA fails entirely, proving that authentication requires another layer of security in order to ensure data protection. A layered approach to authentication starts with “protecting the endpoint, trying to secure the browser, going all the way up to looking at the navigation, building profiles of users and accounts and looking for anomalies, doing that across channels,” says Litan. This kind of identity assessment analyzes endpoint and user data, metadata, and ehavior as it identifies linkages across and between entities.
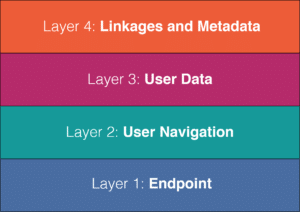
No singular authentication method used on its own is sufficient enough to keep determined fraudsters out. Creating a layered defense system makes it more difficult for an illegitimate caller to access desired information, such as a physical location, computing device, network, or database. If one barrier is broken or compromised, the fraudster still has at least one more barrier to breach before successfully accessing the desired information. This system ensures that each layer defends the previous layer, making it more difficult for a fraudster to circumvent the security of the entire system.
Written by: Mike Yang
Recent Posts
- Pindrop’s ICASSP 2024 paper shows how room acoustics can enhance liveness detection
- Pindrop® Pulse, First to Accurately Detect Deepfakes from OpenAI’s Voice Engine
- 4 Top Cybersecurity Trends Discovered From Our Recent CFX Event
- Pindrop Named A Winner in the FTC Voice Cloning Challenge
- Pindrop® Pulse Excels in an Independent NPR Audio Deepfake Experiment


