The continued success of the modern web relies on nothing so much as data, great roiling rivers of information produced by billions of users and trawled constantly by the network’s insatiable predators. They take in and store as much of that data as possible, and dissect, analyze, and categorize it every which way from Sunday. But those companies also need to secure the data they vacuum up, and some tech providers are finding that maybe they’re better off just not having that data in the first place.
You need look no further than the recent Yahoo data breach to see what the consequences can be of gathering and storing all that user data. Or the Target breach. Or the Office of Personnel Management breach. Or any of the hundreds of others from the last decade. User data has become the most valuable asset on the web, and not just for retailers and tech companies who need fuel for their analytics engines. Attackers covet the same information, and they know exactly where to find it. Any organization that collects and stores that data is a target for cybercrime groups, individual attackers, and others interested in seeing what’s in those databases.
The handful of companies that rule the Internet–Google, Amazon, Microsoft, etc.,–all sell products, whether they’re phones, books, or software. But they’re all essentially data analytics firms, ingesting and generating unfathomable amounts of information about their customers and their behavior and trying to predict what those customers might be interested in next. It’s a fine business, but it’s also one that courts danger. Not only will attackers come knocking, but so will law enforcement, and they will come bearing subpoenas and court orders.
The big web companies know this, of course, but they’ve built their businesses on monetizing data, so they don’t have a great way to unwind that. But some newer tech companies have gone in the opposite direction, deciding to keep as little user data as possible. Open Whisper Systems has given us the best example yet of this philosophy and how it can benefit the company as well as its users. OpenWhisper Systems is the developer of the Signal encrypted messaging app and earlier this year the FBI served the company wit a subpoena demanding all of the information OWS had on two separate phone numbers. One of the numbers turned out not to have a Signal account, but the other did, so OWS complied with the subpoena and gave the FBI everything it had on that number.
“Notably, things we don’t have stored include anything about a user’s contacts (such as the contacts themselves, a hash of the contacts, any other derivative contact information), anything about a user’s groups (such as how many groups a user is in, which groups a user is in, the membership lists of a user’s groups), or any records of who a user has been communicating with. All message contents are end to end encrypted, so we don’t have that information either,” OWS officials said in a post.
Here’s what the company turned over to the FBI:
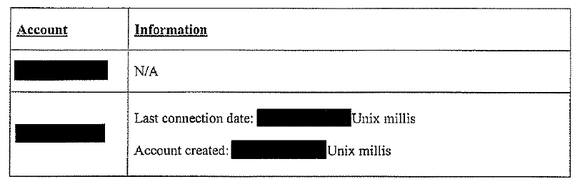
OWS set up its infrastructure to ensure the security and privacy of its users and the messages they exchange. The messages are encrypted in transit and at rest, and OWS does not store any information about users themselves. All that’s needed to get a Signal account is a mobile phone number; no name, no physical address. The kind of data that OWS logs became public Tuesday when the ACLU published documents after a gag order attached to the subpoena was lifted.
“As the documents show, the government’s effort did not amount to much—not because OWS refused to comply with the government’s subpoena (it complied), but because the company simply does not keep the kinds of information about their customers that the government sought (and that too many technology companies continue to amass). All OWS was able to provide were the dates and times for when the account was created and when it last connected to Signal’s servers,” Brett Max Kaufman, a staff attorney at the ACLU Center for Democracy, said in a post.
If the data isn’t there, no one can get to it. Not by compromising your network, and not with a subpoena. It’s a simple equation, but one that few organizations seem to be able to solve right now.
Image from Flickr stream of Claus Rebler.
Written by: Mike Yang
Recent Posts
- 5 Tips for Improving Contact Center Productivity
- Pindrop’s ICASSP 2024 paper shows how room acoustics can enhance liveness detection
- Pindrop® Pulse, First to Accurately Detect Deepfakes from OpenAI’s Voice Engine
- 4 Top Cybersecurity Trends Discovered From Our Recent CFX Event
- Pindrop Named A Winner in the FTC Voice Cloning Challenge


