NRF 2017 Recap: The Current State of Retail Fraud
Last week, Pindrop joined nearly 35,000 attendees at the NRF Annual Convention and EXPO in New York City. According to speakers from the event, retail
Last week, Pindrop joined nearly 35,000 attendees at the NRF Annual Convention and EXPO in New York City. According to speakers from the event, retail
Aite Group, an independent research and advisory firm focused on business, technology, and regulatory issues, interviewed 25 executives at 18 of the top 40 largest
Analysts at Aite Group have identified five key security and service steps that legacy solutions are failing to perform. These are the features that are
1. What are the key challenges of authenticating callers into the call center and IVR channels? Traditional contact center anti-fraud and authentication methods no longer
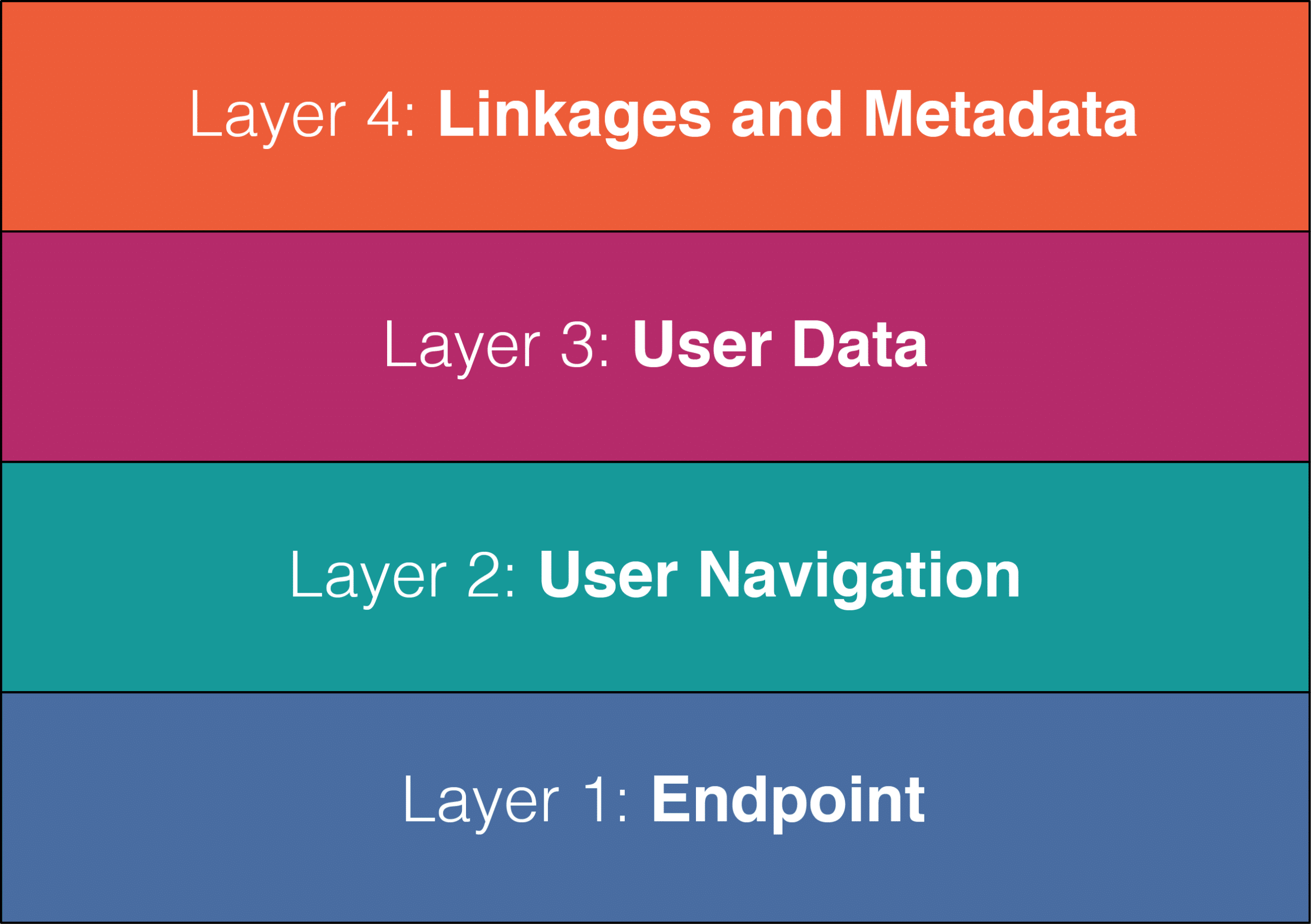
The wealth of information housed by contact centers can be leveraged by fraudsters for data mining and cross-channel attacks. In an effort to prevent phone
Fraud poses a substantial risk to the integrity of federal programs and weakens the public’s trust in government. Though government agencies have made great strides
Aite Group, an independent research and advisory firm focused on business, technology, and regulatory issues, interviewed 25 executives at 18 of the top 40 largest
Contact center fraud attacks have increased substantially in recent years due to the EMV transition and data breaches. Despite the intent to administer positive and
It’s that time of year again. We’ve asked Pindrop Labs researchers to break out their crystal balls and make some predictions for the coming year