
Banking Trojan Lurks in Legitimate Software
Cybercriminals have been relying on the watering hole attack for many years as a consistent method for getting their malware onto victims’ machines. Recently, security researchers

Cybercriminals have been relying on the watering hole attack for many years as a consistent method for getting their malware onto victims’ machines. Recently, security researchers
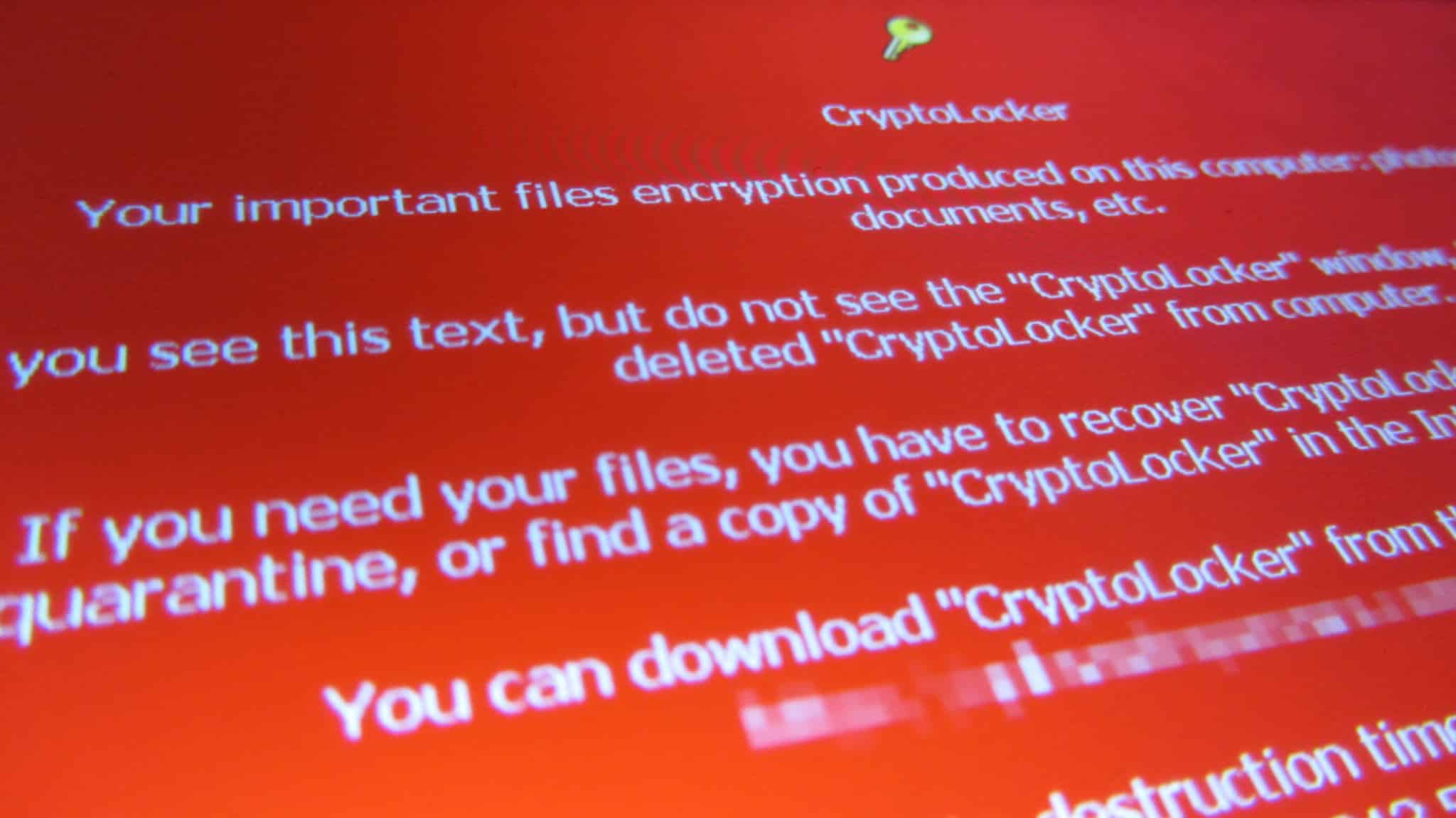
There are few threats that are as commanding as much attention right now as ransomware is. It infects thousands of PCs every day, generates millions
Let’s be honest: The ransomware crews are kind of winning right now. They have a simple, clean business model, a huge victim base, and not

Android users don’t have many things they can point to when it comes to security advantages over iPhone users. The iOS platform is considered significantly safer

Google has released a huge security update for Android that fixes dozens of vulnerabilities, including a number of critical flaws that allow remote code execution.

Ransomware defense is emerging as one of the more important sectors of the security field, with researchers exploring many different paths. One of the key

Researchers have discovered a new backdoor for Mac OS X that gives attackers essentially complete control over an infected machine. The malware is disguised as

As Android ransomware continues to evolve, defenders are trying to keep pace. Most of the efforts to defeat ransomware have come through third-party security software

A new report from House Homeland Security Committee on the encryption debate says that despite both parties being motivated to find common ground, law enforcement