FBI Wants Biometric Database Hidden From Privacy Act

The FBI is working to keep information contained in a key biometric database private and unavailable, even to people whose information is contained in the records. The database is known as the Next Generation Identification System, and it is an amalgamation of biometric records accumulated from people who have been through one of a number […]
Huge Number of Android Phones Vulnerable to Critical TrustZone Bug

A serious vulnerability in many versions of Android that allows an attacker to gain complete control of the target phone by exploiting an app in the secure portion of the operating system still affects about 60 percent of enterprise Android devices, even though a patch was released in January. The vulnerability is in some software […]
Bill Would Prevent Expansion of Government Hacking Powers

Sen. Ron Wyden, who has been a constant critic of the expansion of government surveillance and systematic weakening of encryption, has co-sponsored a bill that would prevent recently proposed changes to federal judicial rules that would give the federal government’s ability to hack the computers of Americans. The bill is called the Stopping Mass Hacking Act […]
Google Allo Brings Encryption, Auto-Deleted Messages

Google’s new Allo messaging app is less than a day old, but it already has attracted a lot of attention from the security and privacy communities, thanks to its inclusion of end-to-end encryption and disappearing messages. Not all of the attention has been positive, however. Allo is a combination app that includes typical chat capabilities […]
Sites Turn to Audio Fingerprinting to Track Users
Researchers from Princeton University, conducting a privacy survey of the top one million web sites, discovered a variety of tracking and identification techniques in use, including a novel tactic that uses audio signals to fingerprint machines and browsers. The Princeton study measured a slew of different stateful and stateless tracking techniques, with the goal of measuring […]
Clickjacking Bug Affects 95 Percent of Android Devices

Researchers have found that a vulnerability in Android that allows attackers to trick users into granting apps elevated privileges affects more devices than had originally been thought–nearly 96 percent of all Android devices. The vulnerability is not a typical bug. It relies on some user interaction and lies in the way that Android allows apps […]
Senator Asks FTC to Examine Issues With Chip Card Rollout

A Senator from Illinois is asking the Federal Trade Commission to look into problems and delays in the process for certifying chip-card payment software systems and whether the group of six global payment networks that controls the process is causing those delays intentionally for financial reasons. Sen. Dick Durbin (D-Ill.) sent a letter to Edith […]
On the Wire Podcast: Alex Howard

Alex Howard has been writing and thinking about technology and open data issues for more than a decade, having worked at O’Reilly Radar, the Huffington Post, and now at the Sunlight Foundation. In this episode of the podcast, Dennis Fisher talks with Alex about the ways in which technology coverage has shifted, the advent of […]
Ransomware Attack and Defense
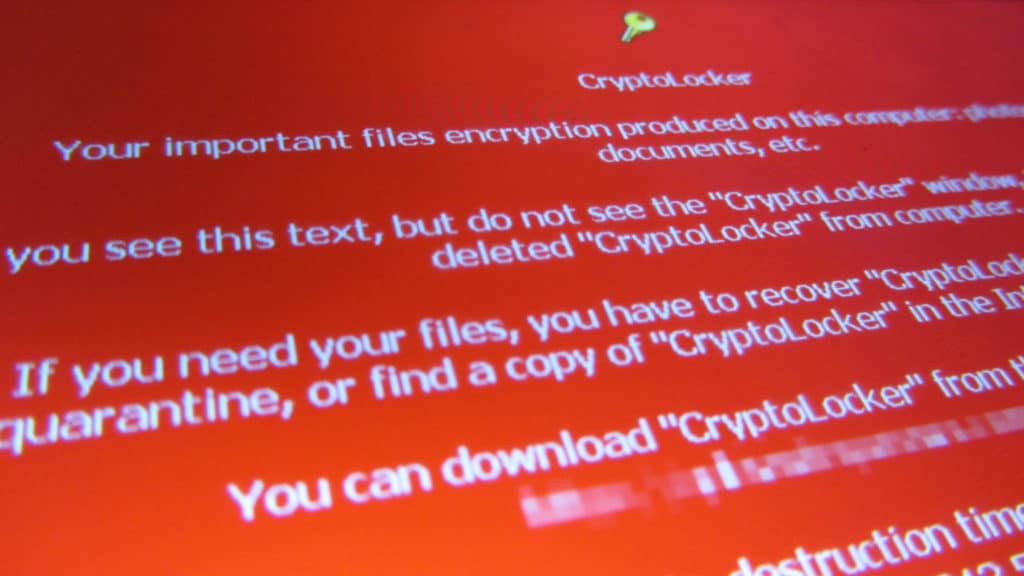
By Jessy Irwin In the US, ransomware is earning a significant amount of media attention for shutting down schools and hospitals, but a recent study points to Canada as the country 4th most likely to be a victim of ransomware attacks. With that in mind, this document presents background information, security recommendations and policy for […]